In this guide, we will learn how to setup secure private docker registry on Ubuntu 22.04 (Jammy jellyfish) using self-sign SSL certificate and htpasswd.
Private docker registry is the repository for container images and it supports both uploading and downloading operations. It is strongly recommended one should always secure private registry to mitigate security risks.
Once we setup secure registry then we can use it in our deployments on Kubernetes cluster or may be in RedHat Openshift Cluster.
Prerequisites
- Minimal Ubuntu 22.04 LTS Installation
- Docker Installation and its daemon should be up and running
- Sudo user with admin rights
- Stable Internet Connectivity
Also Read: How to Install Docker on Ubuntu 22.04 / 20.04 (Step by Step)
Once the prerequisites are met then jump to following steps.
Step 1) Create Credentials for Registry
To create username and password for docker registry, we will use htpasswd command. To make this command available, install ‘apache2-utils ’.
$ sudo apt install apache2-utils -y
Create a folder for saving the credentials file,
$ mkdir -p ~/private-registry/auth $ cd ~/private-registry/auth
Run the following command to create credentials (username & password)
$ htpasswd -c -B -b passwd-file devops P@ssWord32!
This will create passwd-file in current working directory, it will have username and encrypted password string.
$ cat passwd-file devops:$2y$05$rYP/3ohY.yy986ZKvAMGjOF7e7PskCv9x5nV0fLYfm7pWMzrKocOe $
Step 2) Generate Self-Sign Certs for Registry
Before generating the self-sign certificates, let’s create a directory which will store certificate and private key file.
$ mkdir ~/private-registry/certs $ cd ~/private-registry/certs
Now, to generate private key, run following openssl command.
$ openssl genrsa 2048 > domain.key $ chmod 400 domain.key
Run Following command to generate certificate file.
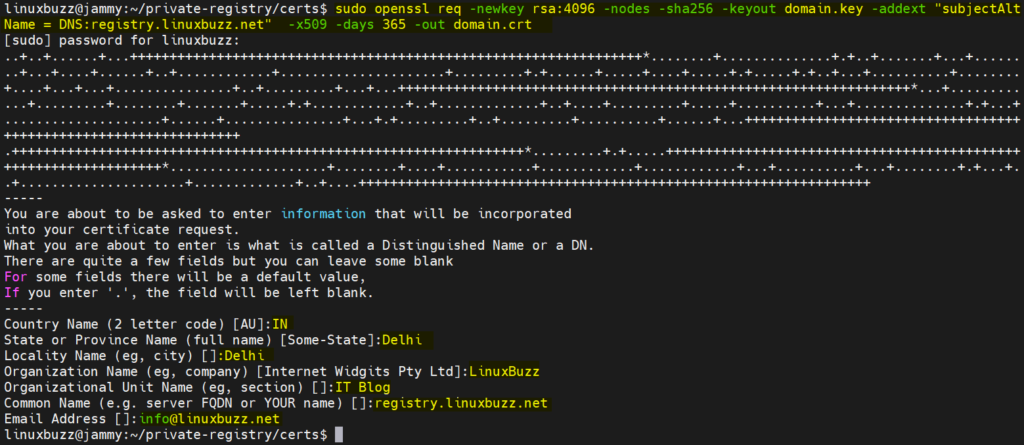
Note: Replace FQDN of registry as per environment.
$ sudo openssl req -newkey rsa:4096 -nodes -sha256 -keyout domain.key -addext "subjectAltName = DNS:registry.linuxbuzz.net" -x509 -days 365 -out domain.crt
Verify key and certificate file,
$ ls domain.crt domain.key $
Step 3) Start Registry Container
Execute the following docker command to start register container,
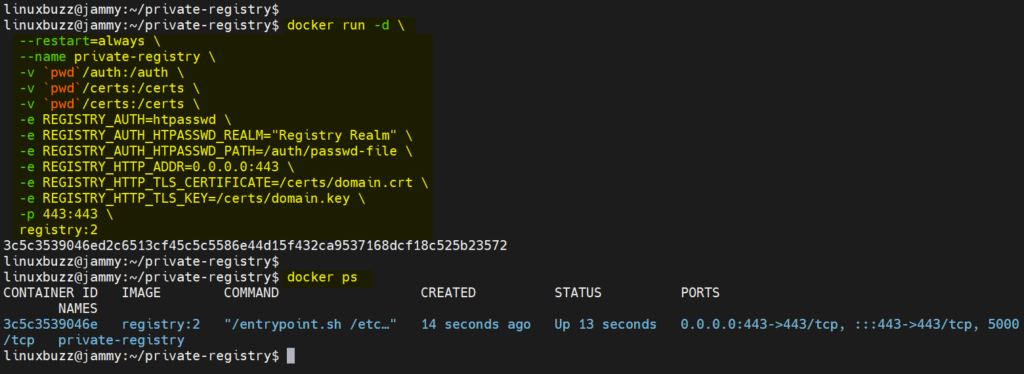
$ cd ~/private-registry/ $ docker run -d \ --restart=always \ --name private-registry \ -v `pwd`/auth:/auth \ -v `pwd`/certs:/certs \ -v `pwd`/certs:/certs \ -e REGISTRY_AUTH=htpasswd \ -e REGISTRY_AUTH_HTPASSWD_REALM="Registry Realm" \ -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/passwd-file \ -e REGISTRY_HTTP_ADDR=0.0.0.0:443 \ -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \ -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \ -p 443:443 \ registry:2 $
View container status,
$ docker ps
Output of above commands would look like below:
Perfect, above output shows that private docker registry is up and running. Let’s do the testing of this registry.
Step 4) Test Private Docker Registry
As our registry is running at URL: https://registry.linuxbuzz.net
Before testing, make sure to add following entry in /etc/hosts file on the system from which we are doing the testing.
192.168.1.167 registry.linuxbuzz.net
Save and close the file.
Try to login to registry using following command, specify the credentials that you have create in step 1.
$ docker login -u devops https://registry.linuxbuzz.net:443 Password: Error response from daemon: Get "https://registry.linuxbuzz.net:443/v2/": x509: certificate signed by unknown authority $
We are getting an error while authentication because we are using self-sign certificate, so to fix this, create following folder and copy domain crt file.
$ sudo mkdir -p /etc/docker/certs.d/registry.linuxbuzz.net:443 $ cd /etc/docker/certs.d/registry.linuxbuzz.net:443
Copy the domain crt file from your registry server to this machine, run following scp command
$ sudo scp linuxbuzz@192.168.1.167:~/private-registry/certs/domain.crt . $ pwd && ls /etc/docker/certs.d/https:/registry.linuxbuzz.net:443 domain.crt $
These steps have configured docker daemon to trust our self-signed certificate.
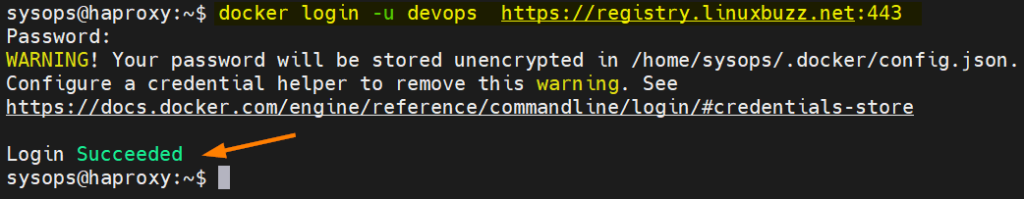
Now, try to login to the registry. This time you should login successfully.
$ docker login -u devops https://registry.linuxbuzz.net:443
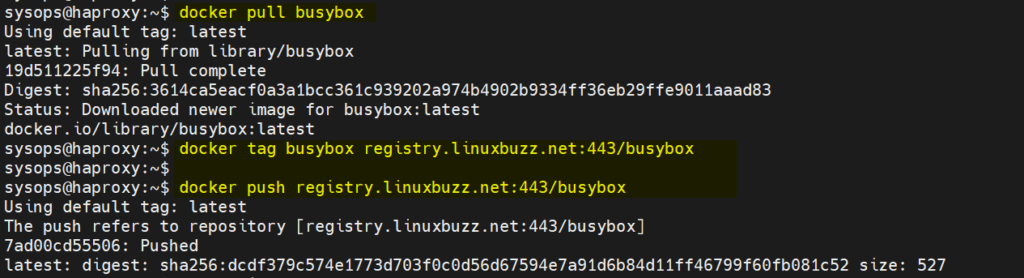
Great, now we have logged in to the registry. Let’s try to push busybox image to this registry.
$ docker pull busybox $ docker tag busybox registry.linuxbuzz.net:443/busybox $ docker push registry.linuxbuzz.net:443/busybox
Output,
That’s all from this guide. I hope you have found it informative and able to setup your secure private docker registry on Ubuntu 22.04. Don’t hesitate to post your queries and feedback below in comments section.
Also Read: How to Set Static IP Address on Ubuntu 22.04